ED25519 (formerly, Proposal 224) is a public-key signature system that is now being adopted by Tor v3 hidden services. As per Tor's official statement on its blog, v2, which relies on older systems of public-key signatures, will be completely deprecated and removed by October 2021.
So, as I was experimenting with Tor in the last few days, I decided to check out tools to help generate these new ED25519 signatures. Out of many out there, mkp224o worked well for me.
Now usually, setting up the dependencies for such C99-based tools is usually trickier in most Windows or MacOS systems than in Linux systems. But, thanks to this docker image which I found on the DockerHub, things were smooth for me.
Let's see how to generate one, then?
It's fairly straightforward with Docker - just run a container from the image, exec inside it and use the tool 🚀
To run a container and exec inside it:
docker run -it nwtgck/mkp224o
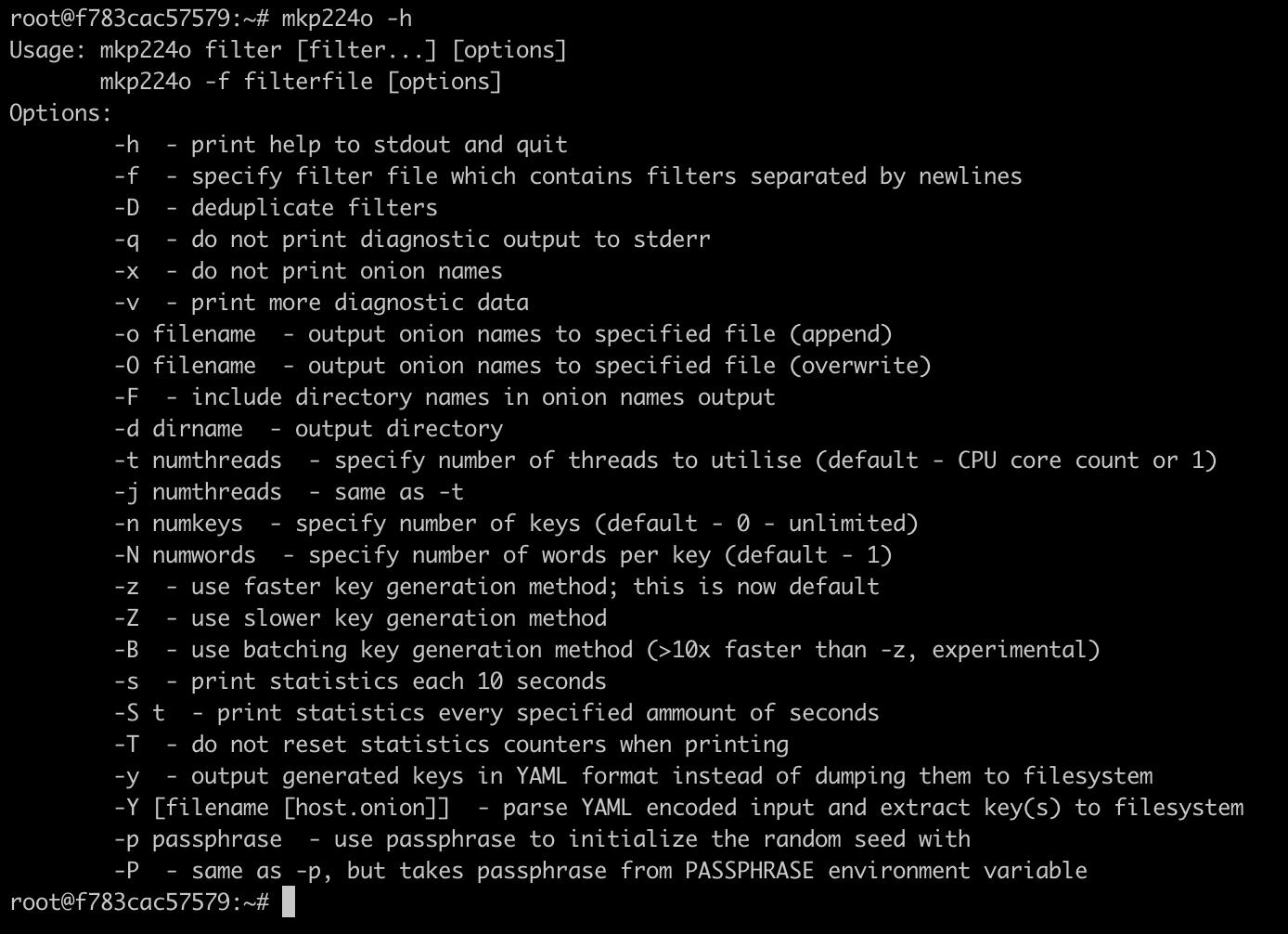
Once you're in, mkp224o will be available to you as an executable. You can check out the usage and options by running mkp224o -h to see a help text like this:
Need a quick-start command to begin with, eh?
Well, got you covered there. Let's quickly see which options are the easiest, to begin with:
-B- Use this for batching the key generation process.-S 1- Use this for printing stats after every second as the generator is running.-d dirname- Use this to output all the generated .onions to adirnamedirectory-n 1- To stop the process after 1 key is matching the filters is found
With all the above options, here's how the syntax to generate 2 keys starting with temp and store them into a onions directory looks like:
mkp224o -B -S 1 -d onions -n 2 temp
And voila, we now have them in the specified directory:
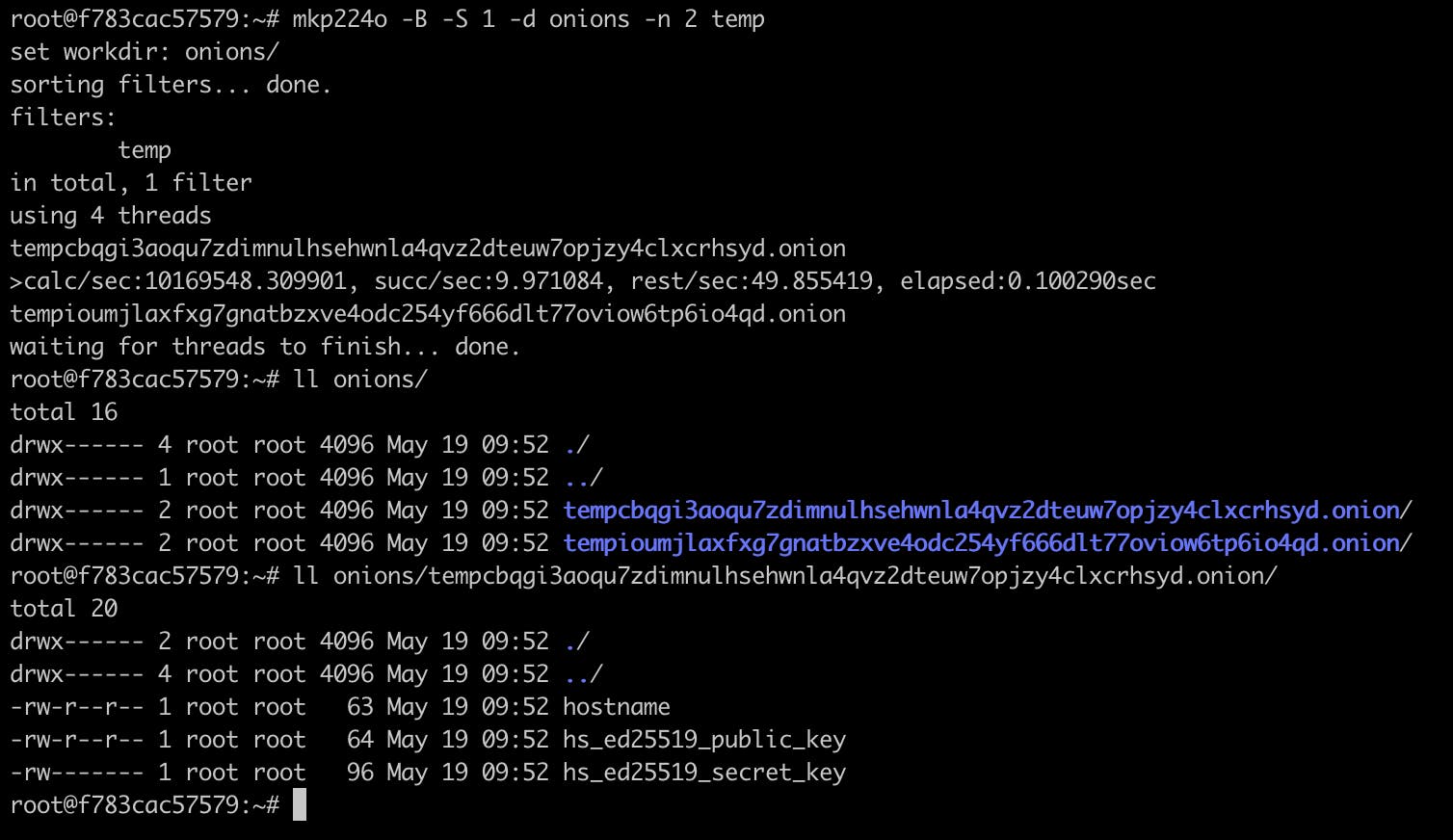
You can find the public key, secret key and a hostname file for each .onion that you've generated.
Happy Tor-ing! 🧅😁